Network Engineering Objectives
- Analyze personal and organizational requirements and design an appropriate networking architecture.
- Develop cloud solutions emphasizing the benefits of remote infrastructure.
- Identify networking misconfigurations and determine solutions to achieve optimal performance
- Demonstrate enterprise network administration through access controls, group policy, remote deployment, and backup recovery.
- Create networking solutions that incorporate traditional networking, IoT, and mobile devices.
- Demonstrate security principles within networking solutions based on industry standards.
Analyze personal and organizational requirements and design an appropriate networking architecture.
Objective 1
Logical and Physical Topologies | NTW275
In this assignment we were tasked with changing a logical network map to a physical network map, and a physical map to a logical map. For each of these we had to account for different IP addresses, devices, VLANs, subnetting, and room placement. We had to take into consideration of the company that we are design the maps for, to understand the layout, requirements, devices, cables and more.
Each of these diagrams needed to have multiple computers, servers, networking, and even smart devices. Every device needed to be represented, ladled, and organized, showing either where they are located, or the logical groups of the devices. I wanted to have these documented look organized and professional, while keeping the knowledge requirement low, so anyone regardless of experience should be able to understand it to some extent.
Physical Map
When designing the physical map I had to understand where reach room would be, and how they would be accessed. Also understanding how to keep critical devices secure, and having user devices accessible.
Organizational Network Design | NTW275
In this assignment we where told to find a company on Indeed, in this case I chose Infosys, and based on the job requirements, we needed to come up with a design for their network. There were three core points that I wanted to focus on with this design, those being Remote Workers, Cloud Computing and Segmentation. Infosys was originated in India, and has locations in Arizona, Texas, Mexico and Canada. Because of this I need to make sure no matter where an employee is, they will be able to do their work. This leads into cloud computing, as based on my research Infosys tends to use Azure, while having public accessible servers, virtual machines, virtual networks, and app hosting. Lastly I designed the network around the Cisco Tetration (CSW), this way there is proper subletting on the network.
Devices
| Device | Price | Usage |
|---|---|---|
| Cisco ASA 5515-X Firewall Edition | $142.41 x 2 * | Firewall with multiple network ports, used on the employee network, and after the modem. |
| Cisco Business 145AC Wi-Fi Access Point | $63.37 x2 | Supports wireless and 2-3 LAN ports, used for the Guest Network, and the Employee network. |
| Cisco Catalyst 1200-48P-4G | $815.93 | Larger switch with 48 ports, use mainly for the Upper Switch in the Employee Network |
| Cisco Catalyst 1200-8T-D | $156.23 | Lower Switch for the IT network with 8 ports |
| HP Z4 G4 Workstation | $418.56 * | Workstation for employees |
* Price Based on Refurbished Listings
Services
| Service | Price | Usage |
|---|---|---|
| Open VPN / Tailscale | Free - Monthly Tiers | VPN For Remote Access, either for encrypting all traffic or just traffic for the cluster devices |
| Azure Networking | $0.01 /GB * | Allow for networking between virtual devices, such as routers, switches, VPN, and machines |
| AKS | $0.10/cluster/hour | Allow for developer tools such as node, app development, API, and SLA |
| NGINX plus | $2,500/year** | Host HTTP/HTTPS, email, and other web services |
| CSW SaaS | $3/month*** | AI based network manager to improve security against attacks |
* Price Varies on Tiers and services
** Price is for cloud hosted service
*** Pricing is not public
Develop cloud solutions emphasizing the benefits of remote infrastructure.
Objective 2
AWS Cloud Architecture | NTS336
Amazon Web Services (AWS) provides all-in-one experience for your company when working in the cloud. With services ranging from access control, storage, security, virtual machines, and more, it can be an excellent opportunity for companies. During this assignment I went over a multitude of different services that AWS provides, and explain how each one is used and is important. This document went over the following services:
- Architecture
- IAM
- EC2
- S3
- RDS
- DynamoDB
- VPC Networking
- Security
- Lambda
- CloudWatch
- CloudFormation
- High Availability
- Scaling
- DevOps
- Deployment
- Advanced Management
Identify networking misconfigurations and determine solutions to achieve optimal performance
Objective 3
Final Project 2.0 (Documentation) | NTW216
This was a group project with: Keven Baquerizo; Giani Saldana; Rashalee Thompson
Roles: Team Leader and Configuration Manager
During the entirety of this class we where setting up a Windows Server, we had to configure services such as Active Directory, Samba, Devices, Users, and troubleshoot issues that our professor did to our servers. For this objective I will be going over specific troubleshooting tasks.
No Internet (26)
On this day we discovered that our account was missing from the sign in screen, this was one of the tasks that we had to resolve. We first went to the other user section, and inputted the username and password for our account, logging us in. Next we noticed that the computer was not connected to internet, when going to the ethernet settings in windows it showed that the adapter was disabled. By going to 'Control Panel\Network and Internet\Network Connections' we could then enable the adapter, resolving both of the issues we had.
System Sate Backup (16)
In this case we where tasked with setting up a system backup. Before we did this we had added a secondary drive, meant for backups, then we configured this drive using 'Windows Server Backup' and 'Local Backup'
Demonstrate enterprise network administration through access controls, group policy, remote deployment, and backup recovery.
Objective 4
Final Project 2.0 (Documentation) | NTW216
This was a group project with: Keven Baquerizo; Giani Saldana; Rashalee Thompson
Roles: Team Leader and Configuration Manager
During the entirety of this class we where setting up a Windows Server, we had to configure services such as Active Directory, Samba, Devices, Users, and troubleshoot issues that our professor did to our servers. For this objective I will be going over specific administrative tasks.
Active Directory (56)
Active directory is a critical part of Windows Server, this works by having a domain, and then adding users to this domain. Each user can be assigned to a group, or have permission set directly. These permissions could be things like elevated privileges, configuration settings, password resets, and more. Active Directory works in tandem with Group Polices, with these two making the baseline of Access Controls.
Group Policy Management (54)
Just like Active Directory, Group Policy allow for in depth and advance permissions with Active Directory. With these policies you can create templates, and even automation. The polices we changed where regarding the windows security, specifically auditing, this is just one of the many things you can control using Group Polices.
Shares (28)
Windows Server is able to host shares, this allows users to open and view files remotely, either wirelessly on the same network, or with a VPN. Windows Shares is native to all windows versions, including home, and they work excellently with Active Directory and Group Policies.
System Sate Backup (16)
In this case we where tasked with setting up a system backup. Before we did this we had added a secondary drive, meant for backups, then we configured this drive using 'Windows Server Backup' and 'Local Backup'
Create networking solutions that incorporate traditional networking, IoT, and mobile devices.
Objective 5
IoT Device Security Analysis Report | NTW233
This was a group project with: Keven Baquerizo
During this class we did in depth research over an IoT device "KSIZPE LED Strip Light", we analyzed the mobile application, and did a hardware analysis of the device to determine how secure it is. We looked into the issues regarding to the connection from the phone to the device, as anyone could control it with no authentication. We also looked into the security risks of the app itself, and looked into the issues with the hardware. In addition to all of these we looked at multiple documents, including the FCC report of the device.
Logical and Physical Topologies | NTW275
In this assignment we were tasked with changing a logical network map to a physical network map, and a physical map to a logical map. For each of these we had to account for different IP addresses, devices, VLANs, subnetting, and room placement. We had to take into consideration of the company that we are design the maps for, to understand the layout, requirements, devices, cables and more.
For this specific objective these maps had to include IoT devices, this meant I had to consider the many security risks that come with adding IoT to your network. In both of these diagrams they are heavily segmented, so that if any of them where to get comprised, the rest of the network would not be at risk.
Physical Map
When designing the physical map I had to understand where reach room would be, and how they would be accessed. Also understanding how to keep critical devices secure, and having user devices accessible.
Demonstrate security principles within networking solutions based on industry standards.
Objective 6
Foobar Controller Mobile



This is a mobile app for the existing software Foobar2000, that will allow you to control your desktop music player, remotely using your phone, tablet, or other smart device. The goal is to provide a great user interface (UI) and user experience (UX), while still maintaining the abundant number of features that foobar2000 offers. The features would include Playlist, Library, Playback Queue, Album Art, LocalLibrary, Lightweight, Customizable, and more. Although foobar2000 is a great freeware application, it is on the older side, but it still has updates to this date, it is also highly customizable with skins and plugins. The goal is to use an open-sourced plugin called “Beefweb”which allows for communication over HTTP to control Foobar2000remotely. I will not be creating the music player (Foobar2000) or theAPI (Beefweb), I will be creating a mobile app that uses Beefweb to control Foobar, while having an easy-to-use UI.
Since this is a mobile application made for Android, we are able to do a security analysis on the app, using MobSF we can validate the security of the application, and apply industry standards and security principles.
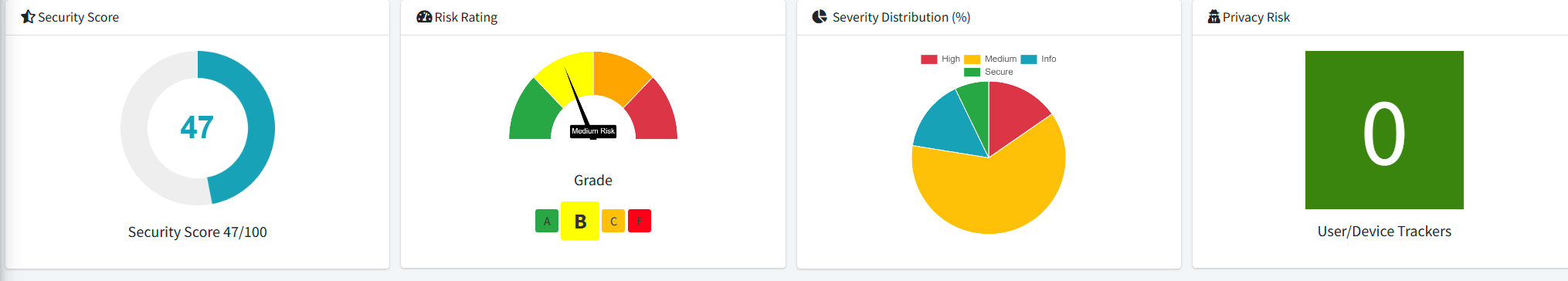
In addition to the MobSF report, the application uses HTTP to handle traffic, although it does not use HTTPS, this is because of limitations with the API. However, the application is meant to only be used locally, and if needed remotely, it works with a VPN. Lastly, the application has multiple validation steps, including ESLint and Dependabot.
GoatDroid | NTW233
In this assignment we were tasked with reverse engineering an IoT application, instead of working with our existing device we were tasked with using Goat Droid. This report gives us information regarding the application, such as warnings about Logging being used, JS enabled in Webview, and more. This information can be critical to understanding the security of your application, or of an application you are using.

